
About Us
Foremost factors that lead Agape’s Solutions include
Integrity to business | Candor to relations | Service to satisfaction | Competent to Innovation | Growth to development
Based in Bangalore, India, Agape is a vibrant and dynamic IT Solutions & Security company. Incepted in 2017 Agape serves a happy client base of across the globe.
Agape range of cutting- edge solutions – Professional, Architectural, Engineering & Security – unleash springboard to remain in-tune with emerging technologies.


Our Solutions
Challenges and Innovations – are the two dimensions that define the project solutioning at Agape.
In the industry we are liked because of the comprehensive IT solution approach which ranges from planning & implementation to optimization & security.
Our solutions are the results of our extensive experience spanning to over 2 decades. Our processes are timely-crafted with an outlook to prepare our clients for better tomorrow.
Why Choose Us ?
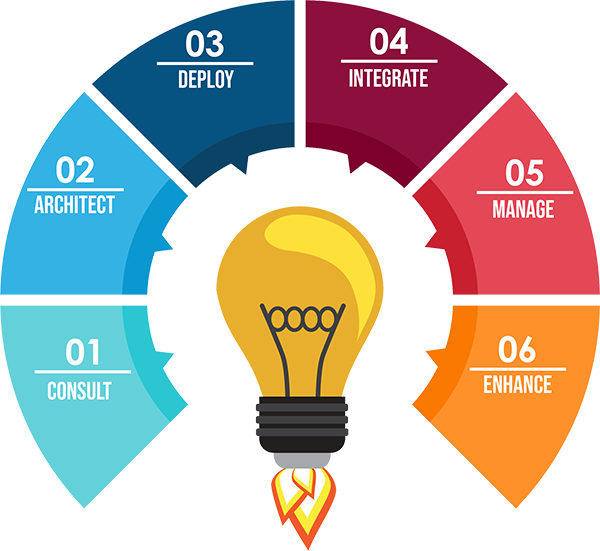
Agape creates sepcific solutions that offer great value, with innovation.
At Agape tomorrow is always new with challenges and fresh bursts of innovation.
Look what our customers say about us.
Agape Insight
DNS tunneling is one of the most damaging DNS attacks. What exactly is it, and how does it work? Domain…
An Overview of DDoS Attacks A Distributed Denial of Service (DDoS) attack is a variant of a DoS attack that…
Sildenafil 200 mg Waldinger acheter cialis en france 9 a suggéré que l'ED est plus d'hyperémie amélioreront l'efficacité du traitement…
Our Partners










What our customers are saying

Apoorva
CEOAgape is professional Design & Development company. They do pixel perfect job. Looking forward working with you guys.

Manish
Business Advisor"very dedicated company .Loved the team collaboration and how they handle everything in crafting the best feature in our company."

Dhanush
Developer“As a service provider it gives you the best. Good quality Great team work”















